Cybersecurity Budgeting:
Risk vs. Cost
How much should we spend on security?
Every security budget faces the same question from leadership: prove it's worth it. This guide gives you the real-world breach data from the IBM Cost of a Data Breach Report 2024 and a concrete ROI framework to make the case — so the next time someone asks "How much should we spend on security?", you answer with numbers, not guesses.
The Security Spending Gap: Where Most Budgets Get It Wrong
Most organizations set their security budget using one of two flawed methods: a flat percentage of IT spend (typically 5-15%) or peer benchmarking ("Company X spends $2M, so we should too"). Neither accounts for your actual risk exposure. The result is a spending gap — either dangerously underfunded or wastefully over-allocated in the wrong areas.
The IBM 2024 data makes this gap visible. Consider a mid-market company with 1,000 employees:
The flat-percentage approach leaves this company $400K short of what the data says they need. That gap translates directly into unmitigated risk: slower incident response, unpatched systems, and no budget for the breach that IBM says costs $4.87M on average for their size.
A risk-based budget starts with your actual threat exposure, then works backward to determine what controls are worth funding. The sections below give you the benchmark data to build that case. (New to ALE and the formula behind it? See our Annual Loss Expectancy resource page for the fundamentals.)
IBM Cost of a Data Breach 2024: The Numbers
IBM's annual report surveyed 604 real breaches across 16 countries and 17 industries. These are not projections or estimates — they are actual costs incurred by breached organizations.
For context: Equifax's 2017 breach cost $1.38 billion in total. Target's 2013 breach exceeded $200 million. These are the outliers that drive the averages up — but the averages themselves are already alarming for organizations of any size.
Mapping Benchmarks to Your Budget
Here's where most CISOs go wrong: they present security budgets as a cost center instead of a risk reduction function. ALE reframes the conversation. The FAIR framework provides a structured methodology for exactly this kind of quantitative analysis.
Example: Mid-Market Company (1,000 employees)
Using the IBM data:
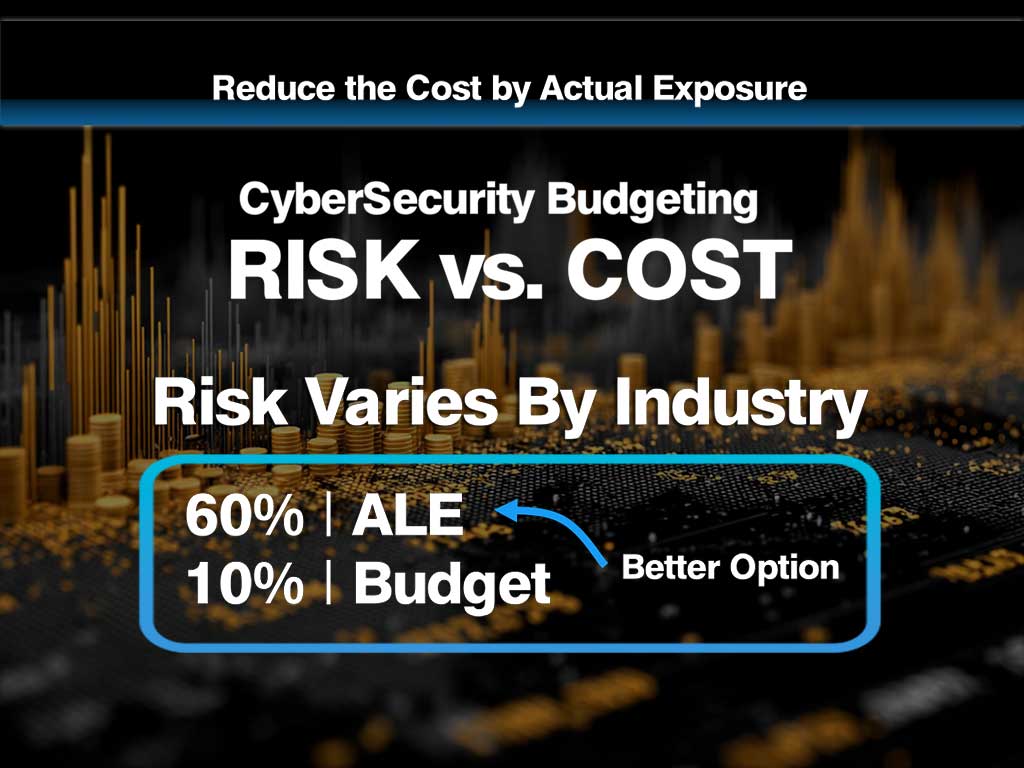
- ALE baseline: $4.87M (expected annual breach cost)
- Current security budget: $1.2M (typical 4–6% of IT spend)
- Security controls reduce ALE by an estimated 60%: $2.92M reduction
- Net ROI: $2.92M – $1.2M = $1.72M in avoided losses
That's not a cost. That's a 143% return on investment. Present it that way.
Example: Small Business (200 employees)
- ALE baseline: $3.31M
- Security budget: $250K
- Controls reduce ALE by 40%: $1.32M reduction
- Net ROI: $1.32M – $250K = $1.07M in avoided losses
Even modest security programs deliver significant returns when measured against real breach costs. CISA's free resources can help small organizations get started without a large budget.
The Budget Justification Framework
When presenting to the board, structure the argument in three parts:
- Baseline risk: "Our ALE — based on industry benchmarks for our size and sector — is approximately $X million per year."
- Control effectiveness: "Our current security program — aligned with the CIS Controls and the NIST Cybersecurity Framework — reduces this by Y%, saving $Z million annually."
- Proposed investment: "This additional $W investment targets [specific threat category] and is projected to reduce ALE by a further $V, delivering a [percentage] ROI."
Every line item maps to a threat, an ARO, an SLE, and a measurable ALE reduction. No hand-waving. No fear-based selling. Just math. The NIST SP 800-30 risk assessment guide provides the formal methodology for documenting this analysis.
Key Cost Amplifiers to Watch
The IBM report identifies several factors that significantly increase breach costs — and others that dramatically reduce them:
- Security skills shortage: +$1.76M average increase
- Non-compliance with regulations: +$1.55M
- Stolen or compromised credentials: +$1.49M (and longest time to identify — 292 days)
- Cloud migration complexity: +$1.12M
Conversely, organizations with AI-powered security tools saved an average of $2.22M per breach, and those with incident response plans saved $1.49M. Understanding where attacks originate — mapped to frameworks like MITRE ATT&CK — helps prioritize which controls deliver the greatest ALE reduction.
Put Theory Into Practice
Understanding ALE in a spreadsheet is one thing. Making budget decisions under pressure — with a boss second-guessing you, a board demanding ROI, and threats escalating through all 18 phases of the Unified Kill Chain — is something else entirely.
Corporate Cyber Defense is an interactive simulation where you manage a security budget against real attack scenarios. Every decision has a measurable ALE impact, every dollar spent must be justified, and the CFO is always watching. It's built on the same IBM benchmarks discussed in this article.
Choose your role. Choose your difficulty. See if your budget strategy survives 18 phases of a coordinated attack.
→ Play Corporate Cyber Defense
Data sourced from the IBM Cost of a Data Breach Report 2024. All figures represent averages from 604 real-world breaches studied between March 2023 and February 2024. Individual organizational risk varies based on industry, geography, security maturity, and attack surface.