FAIR: Factor Analysis of Information Risk
The FAIR (Factor Analysis of Information Risk) model is the international standard for quantifying cyber risk in financial terms. Instead of red/yellow/green heat maps, FAIR gives security leaders a defensible, dollar-denominated way to communicate risk to the board.
How FAIR Works
FAIR decomposes risk into two measurable dimensions:
- Loss Event Frequency (LEF) — How often a loss event is expected to occur. This combines Threat Event Frequency (how often threats act) and Vulnerability (the probability an action results in loss).
- Loss Magnitude (LM) — The financial impact when a loss occurs. Split into Primary Loss (direct costs) and Secondary Loss (stakeholder reactions like lawsuits, fines, reputation damage).
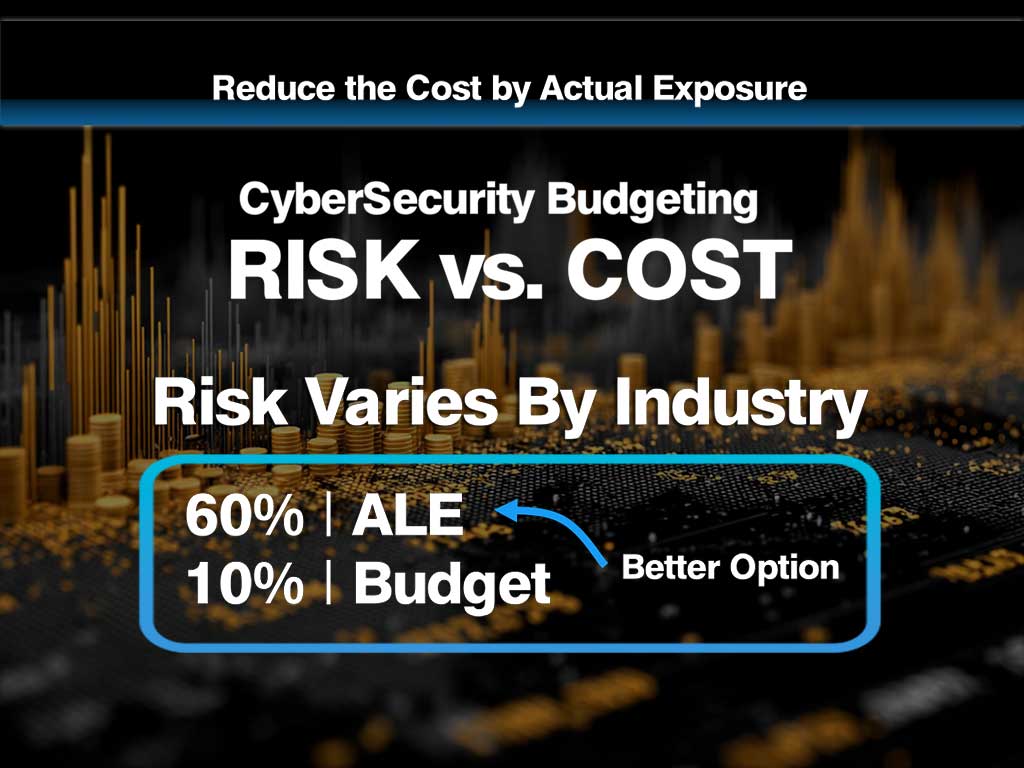
The formula: Risk = LEF × LM, producing an annualized dollar figure — your Annual Loss Expectancy (ALE).
The Six Forms of Loss
Every cyber incident maps to one or more of FAIR's six loss categories, split across primary (direct) and secondary (stakeholder reaction) impacts:
Operational inability to deliver products or services
Costs of managing the incident (IR teams, forensics, comms)
Replacing or restoring damaged capital assets
Regulatory penalties, lawsuits, contractual penalties
Loss of IP, trade secrets, or market differentiators
Decreased stakeholder confidence, customer churn, stock impact
FAIR Cyber Risk Scenario Taxonomy
The FAIR CRM Scenario Taxonomy (February 2025) provides a standardized way to define risk scenarios using four elements. Each scenario follows the structure: "[Threat] impacts [Asset] via [Method], causing [Effect]."
Click each tab to explore the taxonomy:
Threats
Who causes harm — Intent: Malicious & Accidental
Assets
What is at risk
Methods
How attacks happen
Initial Attack Method (Optional)
Effects
Business impact
PRIMARY LOSSES
SECONDARY LOSSES
Example Scenario
Using the taxonomy structure: "Cybercriminals impact customer data via ransomware, causing data breach, business interruption, and regulatory action."
This scenario can then be quantified using FAIR: estimate the frequency (LEF) and the financial impact across all six forms of loss (LM) to produce a defensible ALE figure for your budget justification.
Learn More
- FAIR Institute — What is FAIR?
- FAIR Cyber Risk Scenario Taxonomy (2025)
- Crash Course on Loss Magnitude
- FAIR Materiality Assessment Model (FAIR-MAM)
The FAIR model is maintained by the FAIR Institute and standardized as Open FAIR by The Open Group. The complete CRM Scenario Taxonomy is available to FAIR Institute members.