WordPress Data Breach: Why It Might Never Happen
(And Why It Might Make You Stronger If It Does)
Most WordPress sites have more plugins than they need. It's digital hoarding. "Oh, I might need this social media widget from 2016." You won't. You really won't. But there it sits, unpatched, vulnerable, probably deprecated. It's the digital equivalent of an exercise treadmill in the garage just gathering dust. Don't make excuses, use the treadmill for the intended purpose before it becomes an obstacle.
Should you remove unused plugins? Absolutely. Will you? ...Maybe later. That's what everyone says. "I'll do it later." Later never comes. Later is where security breaches live. Regular maintenance is key—whether you avoid a breach entirely or recover from one, your site (and business) can emerge stronger.

Why a Wordpress Data Breach May Never Happen to You
- WordPress Core Is Actually Quite Secure WordPress powers over 40% of the web, scrutinized by thousands of developers. Most breaches occur through third-party plugins, not the core.
- Hosting Providers Offer Protection Layers Modern managed hosting includes firewalls, malware scanning, and automatic updates that intercept many attacks.
- Basic Security Goes a Long Way Strong passwords, limited login attempts, and keeping WordPress core updated already eliminate the majority of automated attacks.
- You're Not a High-Value Target Most small business websites simply aren't attractive targets for sophisticated attackers. Hackers prioritize sites with large databases of customer information, payment data, or significant traffic.
- The Numbers Are In Your Favor Millions of sites operate safely every day. With reasonable precautions, you're far more likely to avoid a breach.
The Unexpected Advantages If a Breach Does Happen
If the worst does happen, a breach isn't the end—it's often a catalyst for building something more resilient. Here's what you gain:

-
Complete Security Audit and Hardening
A breach forces you to find and fix all your security gaps, leaving you with stronger defenses and a secure website -
Fresh Start With Better Architecture
Rebuilding removes outdated code and creates a faster, easier-to-maintain website with better security built in. -
Established Response Procedures
You'll gain tested processes within your environment, revealing real-world recovery knowledge. -
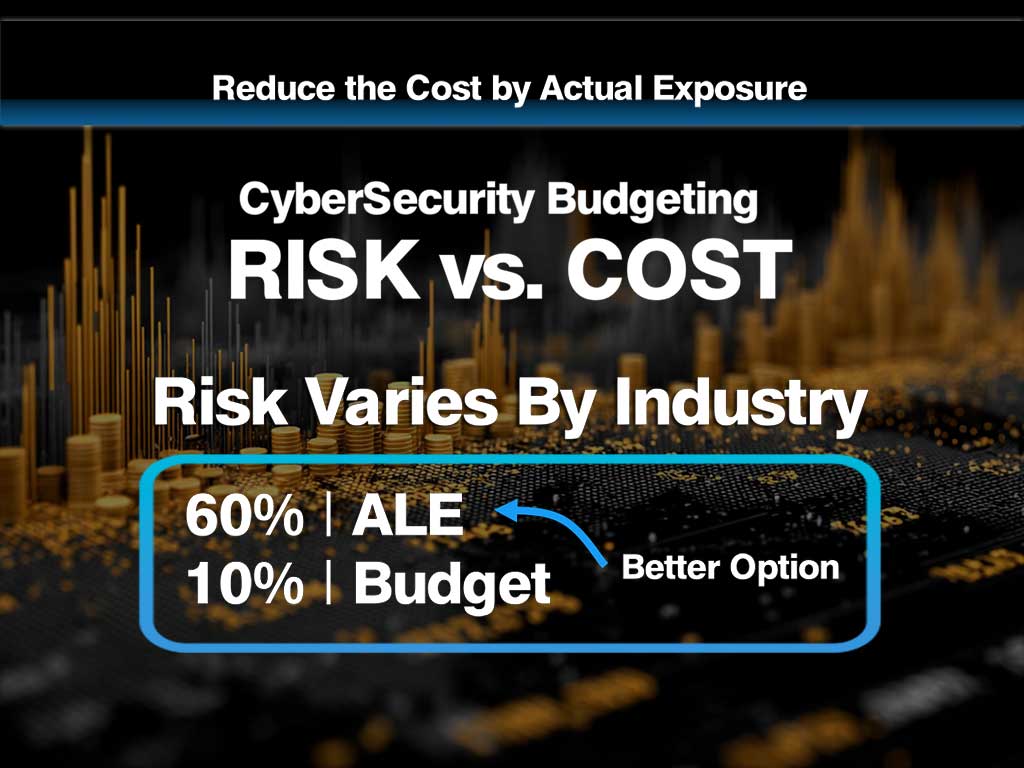
Realistic Risk Assessment
Understaning actual vulnerabilities instead of guessing, so you can focus resources on what matters most. -
Organizational Security Culture
Executives and stakeholders finally understand why security investments matter, making it easier to secure budget and resources for proper protection.
The Real Takeaway
With reasonable precautions—like keeping plugins updated and avoiding weak credentials—you'll likely never face a breach. But if one does occur, the recovery process often leaves you with better systems, deeper knowledge, and greater resilience.
Do you follow best practices or are you someone who understands why they exist?