Cybersecurity Services
Explore our comprehensive range of cybersecurity services and solutions. From network security to threat intelligence, we provide the tools and expertise to protect your digital infrastructure.

Upstream Tech Solutions Laptops
At Upstream Tech Solutions, they’re dedicated to technology and computer rentals for clients of all sizes, whether you need to rent laptops, desktops,...
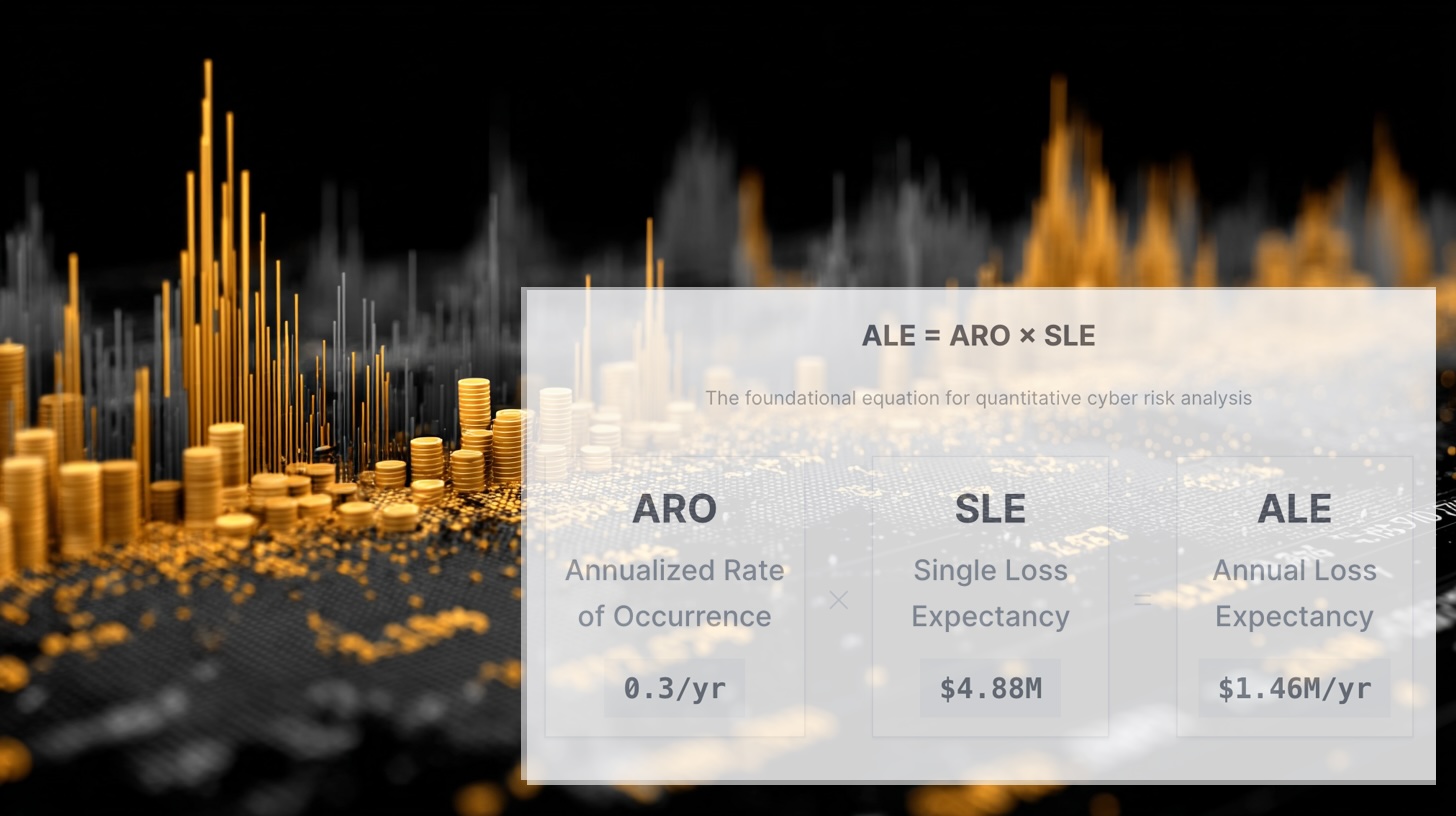
Annual Loss Expectancy
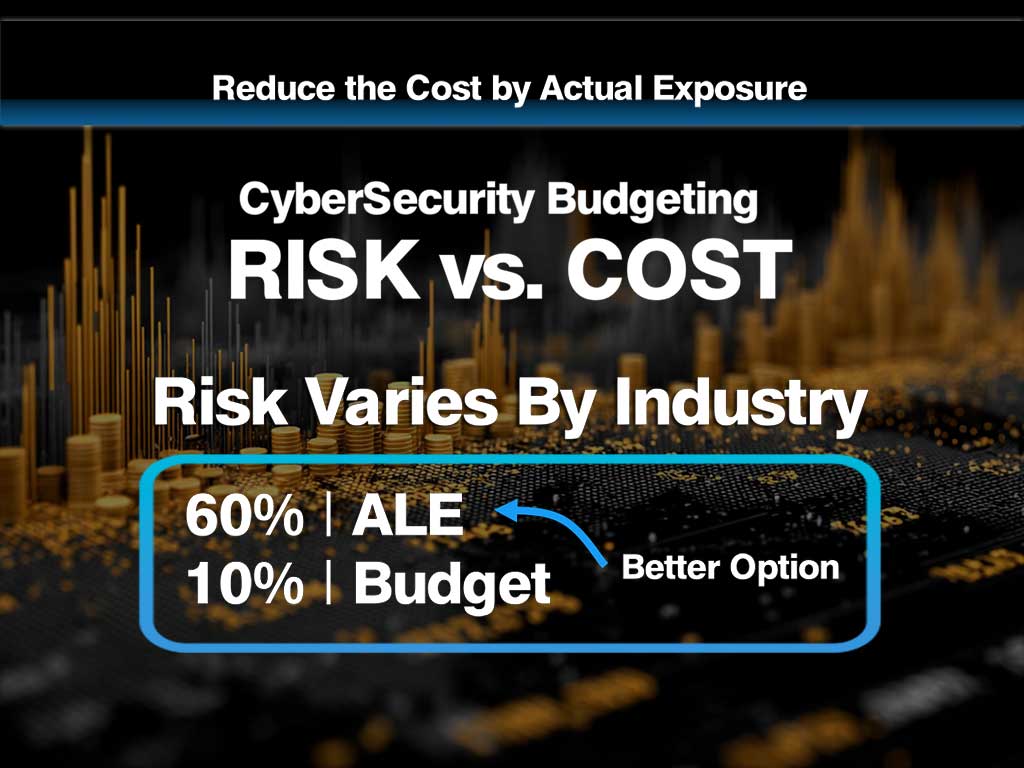
Annual Loss Expectancy (ALE) Annual Loss Expectancy (ALE) is the number you show leadership when "we should probably fix that" isn...

ArkCybr
Zero-Touch Onboarding & Migration 1-click Conditional Access policies (block logins from Russia/China, force MFA on risky sign-ins) Intune auto-enroll...

Endpoint Security
Advanced endpoint protection solutions featuring EDR (Endpoint Detection and Response), anti-malware, and device management. Secure all devices access...

Network Security
Comprehensive network security solutions to protect your infrastructure from unauthorized access, cyber attacks, and data breaches. Our services inclu...
Cloud Security
Cloud-native security platforms designed to protect your cloud infrastructure, applications, and data. Includes CASB, CSPM, and workload protection fo...
Fraud Detection
Fraud prevention and detection solutions using behavioral analytics, machine learning, and real-time monitoring. Protect against account takeover, pay...

Identity & Access Management
Identity and Access Management (IAM) solutions including single sign-on (SSO), multi-factor authentication (MFA), and privileged access management (PA...

SIEM
Security Information and Event Management (SIEM) platforms that collect, analyze, and correlate security events from across your infrastructure. Real-...
Threat Intelligence
Threat intelligence platforms providing actionable insights about emerging threats, threat actors, and attack techniques. Stay ahead of cybercriminals...
Related Blog Posts

