Protect Your Business with
Defense in Depth
A comprehensive, layered security approach designed for small and medium businesses, remote teams, and organizations navigating modern compliance requirements.
What is Defense in Depth?
Defense in Depth is a cybersecurity strategy that employs multiple layers of security controls throughout an IT system. Instead of relying on a single security measure, this approach creates redundant defenses—if one layer fails, others continue to provide protection.
Think of it like protecting a castle: you have a moat, walls, guards, locked doors, and a safe room. An attacker must breach multiple barriers, making successful attacks exponentially more difficult.
Visualizing Defense in Depth:
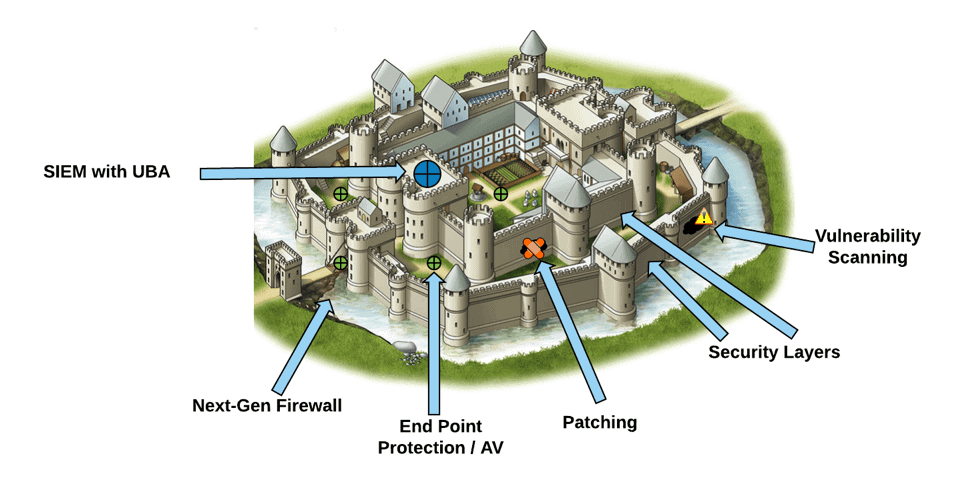
Key Principle: Assume breach at any layer. Design for resilience, not just prevention.
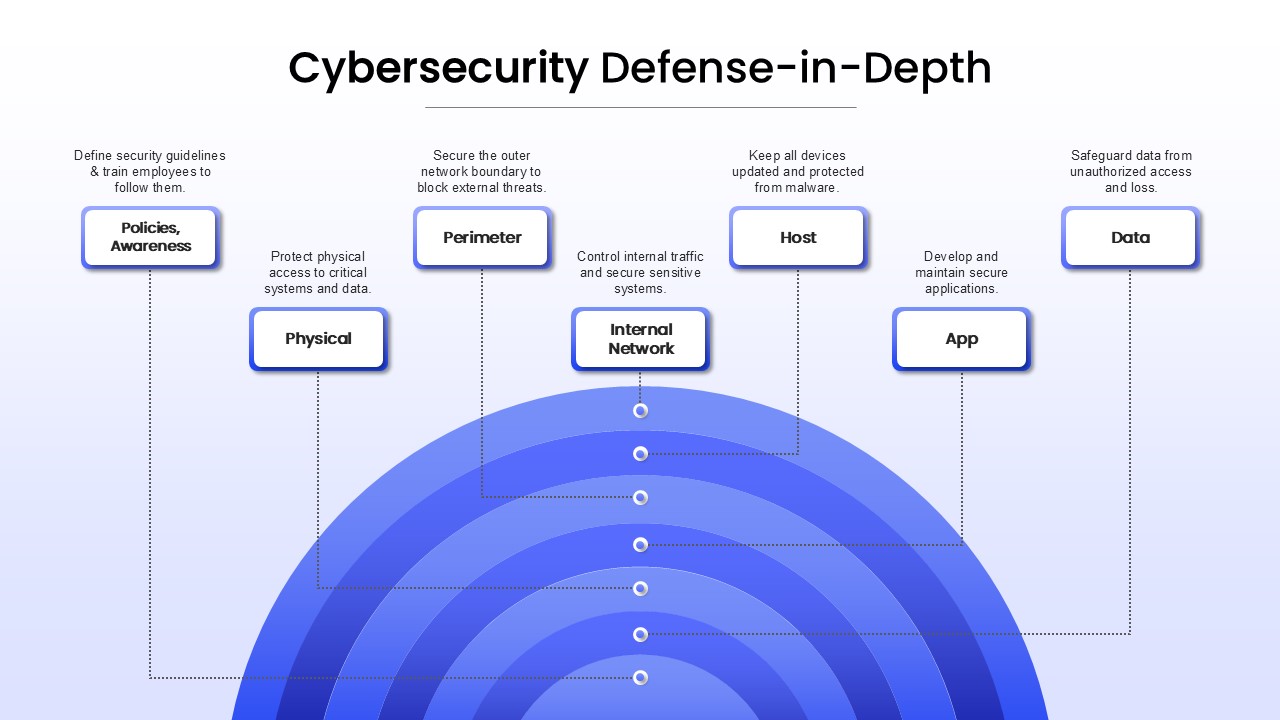
The 7 Layers of Security
Each layer addresses different attack vectors and provides overlapping protection
1. Physical Security
Secure facilities, server rooms, and hardware access. Includes locks, badges, cameras, and access logs.
- Locked server rooms
- Badge access systems
- Security cameras
- Device disposal protocols
2. Network Security
Protect network infrastructure with firewalls, VPNs, network segmentation, and intrusion detection.
- Firewalls (hardware & software)
- VPN for remote access
- Network segmentation
- IDS/IPS systems
3. Perimeter Security
Defend the boundary between internal and external networks. Email security, web filtering, and DMZ.
- Email gateway protection
- Web content filtering
- Anti-spam/phishing filters
- DMZ for public services
4. Endpoint Security
Secure all devices (laptops, phones, tablets) with antivirus, EDR, encryption, and patch management.
- Antivirus/EDR solutions
- Full disk encryption
- Automatic updates/patches
- Mobile device management
5. Application Security
Secure software development, regular updates, input validation, and application firewalls.
- Secure coding practices
- Regular software updates
- Web application firewalls
- Vulnerability scanning
6. Data Security
Protect sensitive data with encryption, access controls, DLP, and secure backups.
- Data encryption (at rest & transit)
- Access control/permissions
- Data loss prevention (DLP)
- Secure backup & recovery
7. User Security
The human layer—security awareness training, strong authentication, and security culture.
- Security awareness training
- Multi-factor authentication
- Strong password policies
- Phishing simulations
Implementation Guide for SMBs
Practical, budget-conscious steps small and medium businesses can take today
Quick Wins (First 30 Days)
-
Enable MFA Everywhere
Multi-factor authentication on email, cloud services, and admin accounts
-
Update All Systems
Patch operating systems, applications, and firmware immediately
-
Implement Backups
3-2-1 rule: 3 copies, 2 different media, 1 offsite
-
Security Awareness Training
Train employees on phishing, social engineering, and password security
Essential Tools (First 90 Days)
-
Business Firewall
Next-gen firewall with IDS/IPS capabilities
-
Endpoint Protection
EDR solution on all devices (laptops, servers, mobile)
-
Email Security Gateway
Advanced threat protection for phishing and malware
-
Password Manager
Enterprise password management for all employees
Hybrid Work Security
Secure Remote Access
- • Always-on VPN for remote workers
- • Zero-trust network access (ZTNA)
- • Cloud-based application access
Device Management
- • Mobile device management (MDM)
- • Unified endpoint management
- • BYOD security policies
Cloud Security
- • Cloud access security broker (CASB)
- • SaaS security posture management
- • Cloud backup and DR
Compliance & Frameworks
How Defense in Depth aligns with common compliance requirements
GDPR (EU Data Protection)
Requires appropriate technical and organizational measures to protect personal data
- ✓ Data encryption (Layer 6)
- ✓ Access controls (Layer 6)
- ✓ Security awareness (Layer 7)
HIPAA (Healthcare)
Safeguards for protected health information (PHI)
- ✓ Physical safeguards (Layer 1)
- ✓ Technical safeguards (Layers 2-6)
- ✓ Administrative safeguards (Layer 7)
PCI DSS (Payment Cards)
Security standards for organizations handling credit card data
- ✓ Network segmentation (Layer 2)
- ✓ Encryption (Layer 6)
- ✓ Access control (All layers)
NIST CSF
Voluntary framework for managing cybersecurity risk
- ✓ Identify, Protect, Detect
- ✓ Respond, Recover
- ✓ Maps to all 7 layers
Need Help Implementing?
Get in touch for personalized guidance on securing your business
⚠️ Security Notice
This is a restricted access environment. Your IP address
(104.23.197.139), activities, browsing patterns,
and access attempts are being monitored and logged for security purposes.
All interactions, form submissions, and page navigation are recorded as part of our intrusion detection and threat intelligence systems.
If you believe you've reached this page in error:
- • You may have triggered automated security controls
- • Your access may require administrative approval
- • You may need to verify your identity
